How you get Internet at home …
Your home network works pretty simple:
You have an Internet modem, router and a centrally placed switch or hub connected to your network devices, wired and/or wireless.
The first point where things will become confusing is the difference between a modem (for cable or DSL), a router and a switch/hub.
So let’s briefly look at how Internet gets into your home – we will start working from the cable that comes into your house provided by your Internet Provider. The first thing it goes to is your modem.
Note : Some (A)DSL systems and some Cable TV systems use a splitter first – some providers have the splitter build into the modem.
This splitter is actually a filter that separates the mixed signals to individual signals.
For example: with DSL, phone and DSL come into your house combined over the same cable. The splitter or filter will separate the signal of your DSL cable to a separate phone signal and a separate DSL signal. Similar methods are used when you get Internet through your TV cable.
Note : Your land line phone is often referred to as either PSTN (Public Switched Telephone Network) or POTS (Plain Old Telephony System). Digital land lines use ISDN (Integrated Services Digital Network), which is more common in Europe than it is in the US.
Your actual Internet data goes over ADSL (Asymmetric Digital Line Subscriber) indicating that upstream data is slower than downstream data, and is often shortened to DSL.
Modem
The purpose of the modem is to connect you to the Internet.
A Modem “decodes” the connection to your Internet provider (ISP). Although “decoding” is not entirely the correct verbiage for that. The proper phrase is Modulate and Demodulate the electrical or optical signal your Internet provider uses to transport data to and from the Internet – in essence it converts an analog signal to digital data.
Systems like Cable TV and DSL use electrical signals (fast). Alternatively modern Internet providers can offer fiber glass or so called optical connections as well (very fast).
What the modem exactly does on that part is not very important, you only need to know that you need one for an Internet connection (it typically also does the login to your ISP).

Old DSL modem
Router
A router can be seen as a data traffic manager.
The router forms a central point in your network and all your network enabled devices are directly or indirectly connected to it.
A router handles the traffic on your network between the connected network devices like for example a computer or smartphone. But that’s not all, the modem we just mentioned is actually also connected as a network enabled device.
The router makes sure that data from one device is properly routed to the device you’d like it to go to. For this to work the router can hand out unique identification numbers to your network devices, the so called IP address – this is called DHPC. When DHCP is being used, the identification of a network device might actually change over time. Therefor the router will need to maintain a list of the identification numbers and for that purpose it has a so called DNS service running – consider it a phonebook with the network devices in it that are connected to your home network.
When you surf the Internet though, all the website you visit have such an IP Address as well but you’re not entering such a number, it would be impossible to remember any of the websites you like. So the phonebook (DNS) we just mentioned should also know how to translate for example //www.tweaking4all.com to the proper IP Address. Maintaining all those millions of websites in your poor little router would be unpractical and therefor your router also consults DNS services outside your house (typically the one provided by your ISP).
Tip: A very extensive explanation of what DNS is and does can be found here.
Switch or Hub
A hub or switch can be seen as a splitter.
The switch or hub allows you to connect more than just one device to your network or router.
Modern setups use a switch, which is basically a smarter hub. It recognizes which network device is connected to what “port”. Hubs on the other hand are old and dumb – they blast the data to all connected devices and are therefor less efficient and slower.
Note : Your wireless network (WiFi) connection is basically yet another network connection and mostly acts as such in a router. Just some additional options (password protection for example) and some additional hardware (transceiver) have been added to accommodate WiFi.

Old network Hub
All-in-One – Modem, Router and Switch Combined
Back in the day, these items were indeed separate devices. You’d have a modem in your basement, connected to (or combined with) a router, and the router was connected to a hub (at the time) that would allow multiple devices to access the network.
With the introduction of broadband Internet (ADSL) pretty quick modem and router became one device, after all, no matter who you are you would need both anyway. You can recognize these modem/router combo’s because they often have only one WAN (Wide Area Network, a.k.a. the Internet) or DSL connection and one LAN (Local Area Network) connection, and no wireless option. Back in the day ISP’s only allowed 1 PC to be connected so hacks emerged quickly to resolve that “problem”.

Combo of DSL modem, Router and Switch
Newer modems actually combine all 3 – which can be sufficient for home use. You recognize these modems because they have one WAN or DSL connection and 3 or 4 regular network or LAN connections. Some also come with wireless, recognizable (most of the time) by one or more little antenna’s. Some combo’s with wireless capability do not show antenna’s as shown in the image below.

Cisco/LinkSys wireless without antenna’s
What does your home network look like?
Each home network setup is of course slightly different, but in the end they all look similar and have the same components, combined in one or more devices or not: Modem, Router, Switch, wires or wireless connections and network enabled devices.
Below a possible diagram of what it might look like, minus some of the devices listed of course …
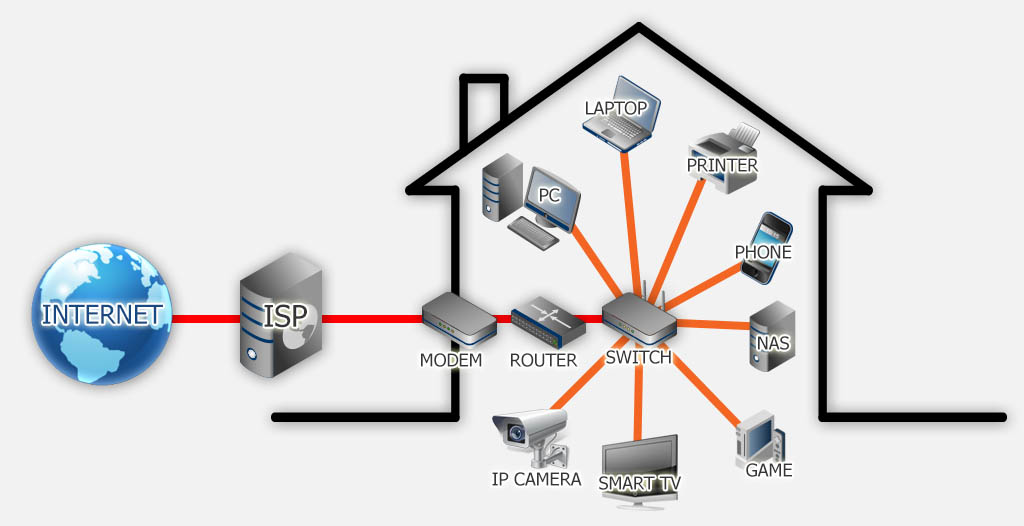
Home Network Sketch
From left to right:
The Internet comes into your home through your Internet Service Provider or ISP.
The ISP provided you with a modem so their data signal can be used by your computer. Most modern modems have router functionality and switch functionality build in – but these can be separate devices. The router is the center of your network as it manages data traffic to and from devices.
The switch, wired or wireless, provides connectivity for your network enabled devices and you might be surprised to see what kind of network enabled devices you can find in your house these days. A switch can also be connected to another switch to expand the number of possible connections or to add wireless capability to a switch that has no wireless build in.
Here a short list of items that come to mind:
- Your desktop computer,
- The laptop you might have,
- A network enabled printer, so the entire family can use it,
- Your smartphone (iPhone, Android, etc), tablet (iPad, Android or Windows), or even MP3 player (iPod),
- A NAS for shared storage (Network Attached Storage, or shared hard-disk),
- Game consoles like the Wii, XBox or PlayStation,
- Your new and fancy Smart TV or that Media Center PC connected to your TV,
- IP Camera’s for security or as a baby monitor
- Internet Radio
These are not the only devices that are network enabled and connected to the switch. Some alarm systems are network enabled, there are network enabled thermostats (for example the awesome Nest), and there are even kitchen appliances like a fridge, oven, washing machine, etc. that are network enabled. I’m sure more will be added in the near future …
Each device in the illustration will have it’s own unique IP Address!
How does you computer get connected?
Now that we’ve covered the physical connection (wired or wireless), what happens when your computer get’s connected?
When you connect your computer (or other network enabled device) to your home network, an attempt will be made to get connected – as you might recall, the router will need a unique identifier which can be handled in 2 ways.
The less used option is a so called Static IP Address. This means that your computer has a fixed IP Address, defined and set in the computer software.
This method is typically used for exceptional situations and/or experts who know what they are doing, so for most common users not recommended (with the exception of a fixed IP Address for modem and router).
To avoid conflict in IP Addresses a more common method used is a Dynamic IP Address: DHCP, or the automatic assignment of an IP Address by the router. On connection to a network, the computer will broadcast a message on the network, asking for an IP Address. The router will answer as it knows which IP Addresses are currently free and not in use, and gives one to your computer. Once assigned the router adds this entry to it’s “phonebook” (DNS).
Note that often both methods are combined in the same network. For example modem and router have a fixed IP Address, where as the computer or so called “clients” have a dynamic IP Address.
The latter (DHCP) is the recommended use for normal situations.
Note : DHCP will not just give an IP Address to the computer. Additional information will be provided to your computer as well. For example the IP Address of the default gateway (modem or router), the IP Address of available DNS servers, etc.
Once connected, your computer can access other network connected devices (if these devices allow this). Data from your computer will first go to the switch, and then to the router, so it can determine where to route it to. Once the router knows where to send it, the data goes back to the switch and the data will be relayed to the device the data is intended for.
Keep in mind that your modem is actually also one of these network connected devices offering something special: Internet access. Your network (except for Internet access of course) would work just fine without the modem functionality.
WiFi Access and Security
Most of us have a wireless network at home for all our gadgets, from Android device, AppleTV, iPad, Laptop, PlayStation, Smartphone, Smart TV, all the way to Wii and XBox.
WiFi is just another network connection, although typically slower than a wired connection and because of it’s wireless nature more sensitive to abuse by others. Because of the the fact that you cannot always see who is connecting to your wireless connection – it could be your neighbor that catches your signal, or a person parked in front of your house just sitting in their car (a.k.a. wardriving). Unlike a wired connected where a person has to physically go into your house to connected their computer to your network.
The security issues you might run into, is that such a person might get access to your private files, copying or deleting them, or even adding garbage you didn’t ask for.
Another big problem could be if that person decides to use your connection for illegal downloading. If such an act is backtracked to you, then YOU will be blamed and not the person that illegally tapped into your WiFi.
Note : Yes – you should consider it to be illegal to tap into somebody else’s WiFi without their permission, after all, so is marching into a persons house and plundering their fridge without their permission. The legal world of course is centuries behind in this, so you might want to check this Wiki page on the legality of piggybacking on WiFi without permission – people in the US and around the world have been arrested and/or fined for this.
This also comes with inconveniences – for example you paid for this nice and fast Internet connection, but everything slows down because the unwanted network participator is sucking all the bandwidth for his or her own use.
Specially in dense populated area, but I would do it even in a rural area, one should password protect their WiFi connection. If available use WPA2, if not pick the older WPA, and if that’s not available consider buying another WiFi modem/router or accept the fact that a WEP protection is very easy to hack.
Additional security measurements can be adding MAC Filtering, where only particular MAC Addresses are allow to access your WiFi (which can be a pain when people come to visit and they’d like to use your WiFi), and disabling the SSID broadcast.
How Secure can my WiFi be …?
None of the currently available WiFi protection methods are really save and can be cracked with a little effort. Reference: How to crack WEP and How to crack WPA.
I do however strongly recommend enabling password protection.
For the more paranoid under us: enable MAC Filtering and disable SSID broadcast as well. Optionally switch your Wireless router off when not used, for example when traveling.
None of these security tools will stop experienced hackers from breaking in to your network, as these are just hurdles for them.
They will however keep out people that try to get into your network that are less experienced in “hacking”.
WiFi SSID is the “name” of your wireless network. To be able to setup a wireless connection, your device needs to know the SSID and because most wireless routers “broadcast” this, your laptop or cellphone will pick it up and make setup of a connection much easier.
Disabling the broadcast of an SSID can contribute to an increased security, but it can be royal pain if you need to setup a new device to connect to your WiFi.
Network Lingo Craziness
You’ve seen the phrases like “IP Address“, “DNS” and “DHCP” a few times now, and might have wondered what it really is. You probably also ran into some funny lingo when setting up your computer as well. I’ll try to explain in the next paragraphs what it all means.
IP Address
As mentioned before, the IP Address can be seen as the phone number of the connected device, and as with a phone number this should be unique.
IP in this case stands for “Internet Protocol” which in essence is the format agreed upon for communication within networks, including the Internet.
IP v4 versus IP v6
IP Addresses come in two types: The so called IP v4 and IP v6, where IP v6 (version 6) is the newer format allowing many more IP Addresses to be used.
IP v4 still dominating …
IP v4 is still very commonly used and dominating, specially in home networks, so expect IP Address in the 129.168.1.100 format when working on your home network.
The old, still commonly used, IP v4 format is build up out of 4 numbers, separated by dots. Each number can have a value between 0 and 255 (a byte). For example:
192.168.1.100
Each computer in your network and the Internet has such a number, and that number must be unique. Which means that theoretically “only” 4.3 billion devices can be connected.
That sounds like a lot, doesn’t it? Well,… it really isn’t all that much if you keep in mind that there are about 700 million websites at the time I’m writing this. Quite a few of these websites have even more than one IP Address … and how about those billions of people at home with their computers, iPads, smartphones, etc …?
So you’re already guessing where this is going – we will be running out of IP Addresses. That’s why IP v6 was designed years ago to “fix” that.
IPv6 is capable of giving 3.4×1038 addresses – which is such a large number that I can’t even come up with a name for it. It’s a 3 followed by 38 zero’s, or 340.000.000.000.000.000.000.000.000.000.000.000.000 devices …
The notation of an IP v6 is very different as well. A IP v6 IP Address is build out of 8 hexadecimal numbers, separated by a colon – which looks funny and will take time for regular users to get used to. For example:
2001:0db8:85a3:0042:1000:8a2e:0370:7334
As you can see – not as easy as the old IP v4. Also not that with IP v6, zero’s at the end can be omitted, so:
2001:0db8:85a3:0042:0000:0000:0000:0000
is the same as
2001:0db8:85a3:0042
Note : Larger web related organizations are already switching over to IP v6. However, switching over to a new IP Address system is cumbersome and will go slow as quite a lot of older equipment is not capable of handling IP v6. It all comes down to enough money …
In the meanwhile a few tricks have been implemented to work with the available IP v4 Addresses and the most important one of those is NAT or Network Address Translation.
NAT or Network Address Translation
NAT allows us to have multiple devices “share” one IP Address. Think of it this way: You have a landline phone at home, with one unique number. To share the phone with family members you could split the phone line and have multiple phones connected to the same land line. You could of course go even further and have a small “Telephone Exchange” or telephone system allowing each person to have their own extension.
This is kind-a how NAT works.
To the outside world (the Internet) you have only one IP Address – the so called Public IP Address (or phone number). In your home however each device has it’s own IP Address which is typically a Private IP Address (phone extension number). The outside world is completely unaware of how many devices (phones) you have in your home – which is a good thing. We wouldn’t want people to know what we have at home and start hacking away.
In the phone example: Your phone system “translates” the connection to the right extension and remembers the connection in both ways – from and to your phone and the caller.
Obviously an outside caller will not be able to dial just one extension directly. System that do allow this, the direct dialing of an extension, act as an operator in between and the caller will still have to dial your home phone number first, get connected to the system and then dial the extension number.
Public IP Address
Your public IP Address can be found in several ways. One of the commonly used (easier to remember) is by going to www.whatismyip.com.
You can also look at Tweaking4All, where we offer you public IP Address in 2 places. When you click your Public IP Address additional browser and lcoation information will be revealed and you can even do a so called IP Trace.
1. Go to the top menu bar, and click on “Info” menu.
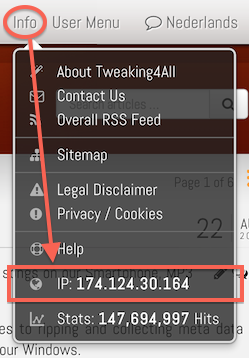
Tweaking4All – Public IP Address
2. In the sidebar on the left, under the heading “Statistics” you’ll find your Public IP Address as well.
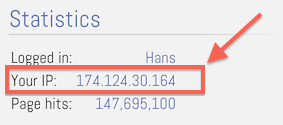
Tweaking4All Statistics
Private IP Address
IP Addresses for private network, like your home or business network, have specific ranges assigned to them to avoid conflicts with IP Addresses in the Internet.
Valid number for a Private IP Address are:
10.0.0.0 – 10.255.255.255,
172.16.0.0 – 172.31.255.255 and
192.168.0.0 – 192.168.255.255.
To better understand how these numbers work, think about how we usually count numbers. Let’s say we have the number 1,000 and we separate the numbers with dots: 1.0.0.0. If we increase 1,000 by 1, we get 1,001 or with the dots 1.0.0.1. If we increase 1,000 by 10 we get 1.0.1.0, and so on. The same mechanism is being used for IP addresses, but instead of 0 – 9 for each “position”, we use 0 – 255. So when we add 1 to the IP Address 192.168.1.0 we get 192.168.1.1. If we add 256 we get 192.168.2.1 and so on … (I hope that made sense  ).
).
The most commonly used private IP address range is the 192.168.x.y, which is also the most narrow range but still offering you to connect 65,535 devices in your private network. The 10.x.y.z range offers 16 million devices, and the 172.16.x.y – 172.31.a.b range offer 1 million devices. I don’t think many people will exceed the initial 65,535 devices in their home … if they do: please invite me over, I’d be curious to see your home … 
Keep in mind that these private IP Address cannot be seen by someone outside of your home (i.e. the Internet).
This is also the reason why accessing your devices when you’re on the road can come with challenges.
Localhost
There is one “Special” IP Address namely the IP Address of the so called “localhost“.
“Localhost” is the device you’re working on and always has the IP Address 127.0.0.1 which is only seen on that device so a device can use network protocols to talk to itself. Each network enabled device has this “localhost” and each device has the same internal IP Address for this.
Default Gateway
The “Default Gateway” is your access point to another network – in a home network this is the access point to the Internet. In a modern setup this will be your modem. The computer needs to know this, so it can access the Internet properly. Granted – it’s more complicated than that, but this simplified explanation will be sufficient for now.
DNS Servers
We have talked about the DNS Service of your router before. The “phonebook” in our phone analogy. And we also know that one of it’s functions is to translate whatever you type in your browser to an IP Address for proper data routing, and that maintaining a list of all websites in the world would be way too much for your poor little router and that it uses an outside DNS service to complete these calls.
The reasons why maintaining this all in your router is impractical is not just because of the vast amount of data, but also because IP Addresses of websites do change, so a very frequent update of a truck load of addresses is required. We’d like to avoid this unnecessary data transfer, so we rely on outside servers to do this for us.
In the phone analogy, think of the DNS list in your router as your personal address-book versus the phonebook provided by your phone company being the DNS service provided by an outside party.
Your Internet Service Provider (ISP) provides such a service and typically tells your modem/router what the IP Address of their DNS servers are. Like you router, most Internet Service providers use DHCP and this means that their DHCP server will provide DNS information to your modem/router.
You can of course also resort to (sometimes much faster and more secure) DNS servers from either OpenDNS or Google. To use these other DNS services you will have to tell your router about this – which is something I’d stay away from until you’re comfortable playing with the settings of your router.
If you would use them just for your computer, then your computer might not be able to find the private IP Addresses of your devices at home since the external DNS server does not know about them.
These are the current IP Addresses for these free, faster, and sometimes more secure, DNS servers:
Public DNS Servers
| Google |
DNS 1 |
8.8.8.8 |
|
DNS 2 |
8.8.4.4 |
| OpenDNS |
DNS 1 |
208.67.222.222 |
|
DNS 2 |
208.67.220.220 |
Subnet Mask
Subnet masks are basically used to indicate how “big” your home or business network is, and allows you to limit or divide a network – something you’d typically not do with a home network, so the explanation of “subnet mask” will be very short in this article.
Simplistically said, a subnet mask of 255.255.255.0 (which is the most common one to use in a home network) means that for any IP Address of a device in your home network, the first 3 numbers are “fixed” (255) and the 4th number is variable (0). Which means that in a 192.168.1.x network, your can have IP Addresses from 192.168.1.0 to 192.168.1.255. This allows 256 devices to be connected in your network. An alternative notation for this particular setup would be 192.168.1.0/24 or Class C network.
Most network experts will get a heart attack because of my simplification of things, but this article is not written with subnet masking methods and high level of expertise in mind … for more details see this article.
MAC Address
A MAC Address, or Media Access Control Address, is another unique identifier for a network enabled device. Basically every network connection, wired or wireless, has such a number. Keep in mind that each network “connector” has it’s own MAC Address, so if your computer has a fixed network connection, then this has a MAC Address. If the computer also has a wireless netwrok option then the wirless has a different MAC Address. In that example your computer has 2 MAC addresses.
This number, unlike an IP Address, is hardware specific and cannot be changed. The DNS service matches this MAC Address up with the IP Address it gave your computer, so we do not only know that it’s your phone number, but we also know your physical address, in the phone book analogy.
I have to say that the MAC Address is not changed in most normal cases, because certain router are capable of mimicking a MAC address that is not theirs, which originates from the days where an ISP allowed only one computer to be connected to the Internet. To make the ISP think it’s only one computer, the MAC Address will be copied from the computer that you used to sign up with your provider. Changing the MAC address, for experienced users, has become trivial.
However: I cannot recommend beginners to start tampering with the MAC Address,… unless you really know what you’re doing!
This MAC Address however can be useful to block or allow specific devices on your network. For example when you’d like to avoid that others use your WiFi (besides the password you’ve set), you could create a list of allowed devices. Somebody who’d try to get access would be blocked since their MAC Address is not in your allow list.
A MAC Address is build out of 6 hexadecimal numbers, separated by a dash (01-23-45-67-89-AB) or colon (01:23:45:67:89:AB). Each number can again be 0 – 255 (in hexadecimal: 00 to FF).
On most network enabled devices you will be able to retrieve the MAC Address from the manufacturer sticker, although sometimes not separated by dashes or colons. The sticker can typically be found at the bottom, the back, or for example the battery compartment of your device.

MAC Address on manufacturer sticker
IP Ports
To make things even more complicated, the network uses so called IP Ports, represented by a number from 0 to 65,535. IP Ports can be seen as “channels” for particular traffic and the first 1000 or so ports are used for typical applications. The remaining other 64,000 ports can be used for all kinds of applications. See IP Ports as a means to prevent total choas when it comes to communication – so that data for your email program does not get mized up with the data for your chat program or web-browser.
As an example, the data your browser pulled in from this website went through port 80 (HTTP). Email is typically send through port 25 (SMTP) and received through port 110 (POP3). Secured email uses again different ports.
Traffic of such a particular kind, can however be send over another channel, that’s why you sometimes see websites that send data through port 8080 (http://www.example.com:8080).
A regular user will have little active interaction with IP Ports unless you’re using a firewall or like to access particular devices in your house from the outside world.
A firewall will potentially block a port for security reasons, preventing specific applications to work.
Firewall
A Firewall‘s sole purpose is to regulate what traffic is allowed to pass through in either direction. So it allows or blocks data to or from your computer with the intend to protect the end user, network or company against malicious situations. This can be to prevent viruses to spread, your child to visit the wrong kind of websites, employees from using the Internet at work for not work related activities like chatting or downloading, or outsiders from entering your network.
In part, a NAT will fulfill a similar function, albeit in just one direction. Outsiders (Internet) cannot see your computer behind NAT. This is no guarantee that things can’t go wrong though.
Most firewalls are software based and run on your computer and/or your router (your router is in essence a tiny computer).
In all cases, a firewall enabled on your router is highly recommended. A firewall on your computer is optional but can be good to have.
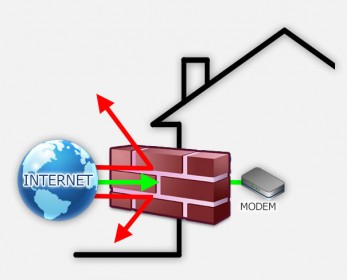
Firewall
Some well known and mostly free Firewall programs for your computer:
Proxy and Cache
A Proxy or Proxy Server acts as a connection point between one point and another. In user terms, most commonly between your computer and the Internet.
Back in the day, proxies were used to limited access to the Internet, or as a means to cache contents when Internet connections were relatively slow. With Caching we mean that if multiple users access for example Google.com, then the proxy cache will store a copy of the Google logo locally on first access. When the next user tries to go to Google, instead of downloading the logo from Google.com, it will be pulled out of the proxy, which will save bandwidth and increase Internet access speed.
Nowadays, I see proxy mostly used to protect your privacy by means of so called “Public Proxies“. Instead of revealing your Public IP Address at the web-server you’d like to visit, the Public IP Address of the proxy will be detected, making it more difficult to determine who is retrieving this webpage. It’s a nice concept and it works, although no guarantees that your privacy is 100% covered, but it can be horribly slow.
Again, a regular user will have no interaction with proxies.
TCP versus UDP
Both terms are even more technical than the ones before as it describes the way little data packets are being send from point A to point B.
TCP (Transmission Control Protocol) or TCP/IP is commonly used for data where we need o be sure it arrived and that it arrived correctly without errors. For this reason the TCP protocol has more overhead for handshaking and error correction and a solid mechanism to verify to content of each packet with the sender.
TCP is used for the majority of data we transmit over a network or the Internet.
UDP (User Datagram Protocol) or UDP/IP is used for data where we don’t really care if everything arrived error free and for example timing is more important than losing data. The lack of all these extras makes this protocol much more lightweight and faster than TCP/IP, but unsuitable for data like programs you download or viewing a webpage.
UDP is commonly used for applications like a video feed or gaming.
As an end-user you will only be confronted with this if you’re doing Port Mapping or Port Forwarding since you will need to device what kind of traffic it involves.
Port Mapping – Or how to access your device from the Internet
Now that we’ve read a little about the lingo, on to more advanced and practical stuff: Port Mapping or Port Forwarding.
As you might recall, most modems utilize NAT (Network Address Translation) to share on Public IP Address. Since multiple computers, or otherwise network enabled devices, can access the Internet, a router will keep track of existing connections or sessions, so it knows when data comes back from the Internet, where to send it. This is required since multiple users might go on to the Internet to look at webpages.
You might recall that for browsing the web IP Port 80 is typically used, so if data comes back on IP Port 80 with the information your browser asked for, the router must know what data to send to what computer.
This is also the reason why a “hacker” randomly blasting data to a modem from the Internet will not do much. The router after all is not aware of a connection or session related to the data – it doesn’t know where to relay it to, so it will ignore it.
As you can see: a great advantage! But … it’s also a disadvantage. What if you’re at work or traveling and you’d like to access your computer at home? There would be no initial session started from your home computer to your say cellphone. Again: the router wouldn’t know what to do with your request as no session exists.
This is where Port Mapping or Port Forwarding comes in handy.
With Port Mapping we designate a particular IP Port (or multiple ports) to be relayed at all times to one particular device in your home network.
Note : This can be security risk of course since you’re opening a hole in your NAT straight to your computer, IP Camera, or which ever device you’d like to reach. Make sure the device you’re forwarding to is benign or protected in some way against malicious folks that like to poke into your network. An IP Camera for example can be considered benign, a fileserver however (your NAS for example) might need some protection.
Once an IP Port is mapped as such, your device can be reached through it’s Public IP Address combined with the port or ports you mapped.
For the example of an IP Camera:
My IP Camera is using port 80 so I can access the video feed through my web-browser. This works in my Home Network perfectly fine.
Now with port mapping I map say port 81 to the Private IP Address of my IP Camera, redirecting it to port 80.
So when I now go to my browser and type my Public IP Address followed by a colon and the IP Port number 81, my router will give me save passage and I can see the video feed of my IP Camera when I’m on the road.
Not always easy …
Port Mapping or Port Forwarding is not always as easy as it sounds – a great resource for guides on how to do this for most commonly available modems and routers is PortForward.com.
Also note that just forwarding a couple of IP Ports is rarely the complete solution – Consider using a Dynamic DNS service as well (see next chapter).
To illustrate how confusing it can be at times, the settings I have to do in my router (different for each router!).
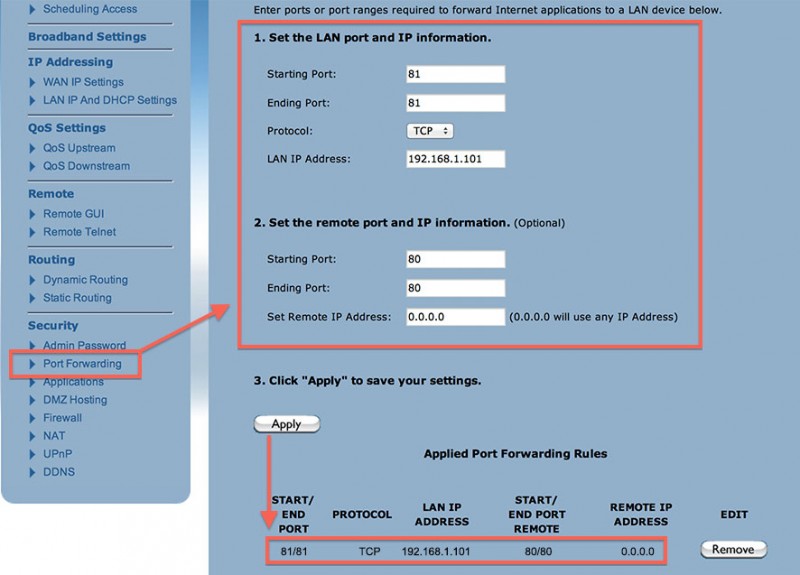
Port Mapping in my ActionTec router
Dynamic DNS
A problem with the Port Mapping or Port Forwarding scenario is that Internet Service Providers can change IP Addresses over time. When ever your modem disconnect and reconnect to the Internet, a potential new Public IP Address might be assigned to your modem.
Note : Some providers use or offer so called fixed IP Addresses. Sometimes by default, sometime at extra cost. With a fixed Public IP Address you will not experience these problems. Although DynDNS can help you giving your connection a more human name like http://myhouse.dyndns.com.
So when you’re traveling (for example) and your home had a power outage, or your Internet connection temporarily got disconnected, then the Public IP Address might have changed. So you do not only have to remember a bunch of numbers, you’re not even sure if it works when you need it.
This is where a Dynamic DNS or DDNS service comes in play.
Most modems, IP Camera’s and some NAS devices support the use of these services. Some are free, but the really reliable ones come at a cost (say $25/year). For those that do not have a modem or NAS (Network Attached Storage) that support a Dynamic DNS service: most of these services offer applications that can be ran on a computer as well. That computer though has to be in your home network and powered on!
My modem for example supports the following (not free!) Dynamic DNS services:
My QNAP NAS supports:
There are free services out there, but I’ve noticed over the years that they all go commercial in the end.
DynDNS.org is the winner?
As you can see, the common dominator is DynDNS.org which has served me very well in the last 10 years and I’ve found them to be very reliable.
This doesn’t mean that the other services are not good in anyway – just the support by devices like your modem, IP Camera, NAS, or other devices can be rather poor when it comes to automatic updating.
What a Dynamic DNS service does, is reserve a (sub)domain name for you, and whenever the Public IP Address changes, your modem will notify the service and the domain will be relinked to the right Public IP Address.
This setup will give you an easy to remember name (for example http://ipcam.athome.com) that stays in sync with your Public IP Address. So when you’d like to access for example your file server or IP Camera from your phone or laptop, you simply go to http://ipcam.athome.com (for example).
Below a few snapshots what these settings look like in different devices:
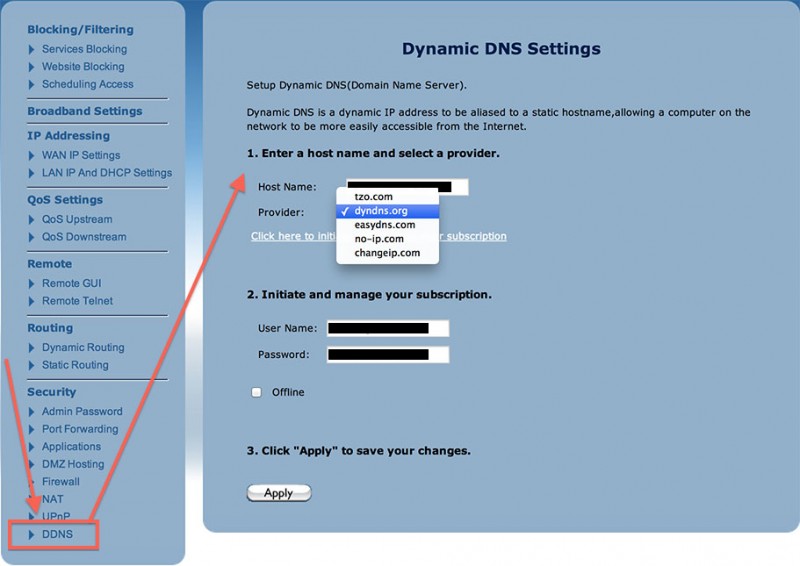
Dynamic DNS setup for an ActionTec Modem
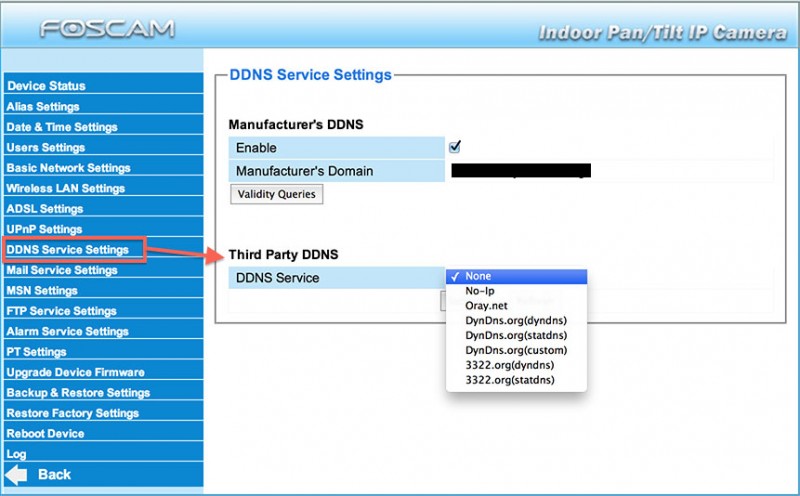
Foscam IP Camera’s support Dynamic DNS
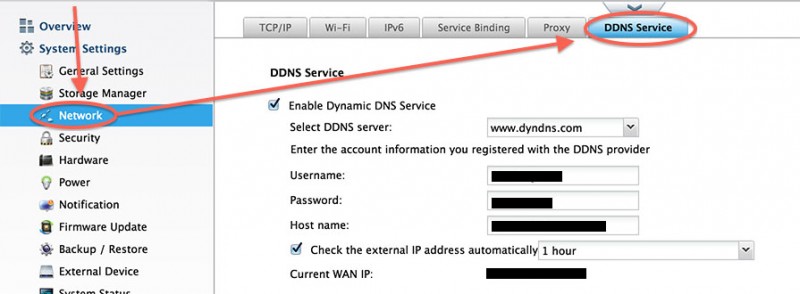
Dynamic DNS Setup on a QNAP NAS
VPN – Virtual Private Network
Another way to access your home network from the Internet is by using a so called VPN.
A VPN, or Virtual Private Network, allows computers from different locations to think they are in the same private network. Setting up a VPN can be done on 2 levels: on the level of your computer, or have your modem, router, or dedicated VPN device do this. The advantage of using a device is that you can potentially make your entire home network part of this VPN, which could also be seen as a disadvantage of course – it all depends on your purpose to have a VPN.
For example, when you’re on the road, your laptop that is connected to your home (or business) network over a VPN connection. Users at home will see your laptop appear in the home network, as if you’re sitting in the next room. Your laptop on the other hand will see the devices in your home network (that are connected to the same VPN) as if you were at home. In this example seeing the entire network would be great. Your modem (or router) handles a VPN connection for your home network, and your laptop handles the VPN on the other side for one user (your laptop) only.
Another way of using a VPN is by connecting 2 networks over VPN together, for example my home network and the home network of my sister, so we can share resources.
VPN however is most often used for business purposes so that colleagues can see each other in the same private network. But VPN can most certainly also be used for home networking as well. A more recent and increasingly more popular use of a VPN is for secure downloading of for example BitTorrents, often through a paid service. Be warned though: VPN is more secure but still not 100% guaranteeing your anonymity you when you’re using BitTorrents for illegal downloading of movies, applications and music.
A downside of VPN’s is that setting them up can be daunting and VPN connections tend to be slower due to the additional overhead for managing traffic and proper encryption. All this has improved in the last years, but it can still be quite challenging.
Unfortunately, I haven’t seen many DSL or Cable modems that provide VPN out of the box, but the majority does allow a VPN connection to pass through the modem.
DMZ – DeMilitarized Zone
The DMZ or DeMilitarized Zone is probably the most dangerous way of opening your home network to the outside world.
With DMZ you designate a computer in your home network to be fully open to the outside world (Internet) – which makes accessing easy. Not just for you though, but also for people that should not have access.
Do NOT use DMZ unless you know exactly what you’re doing and what the consequences are.















Comments
There are 4 comments. You can read them below.
You can post your own comments by using the form below, or reply to existing comments by using the "Reply" button.
Hi.
Can I use my iPhone as a camera with a SIM card and a mobile Internet 3G network,
where there is no home WIFI signal.
Of course I mean to upload for example in the car.
Thanks for the reply and best regard,
zeljko
Zeljko
Hi Zeljko,
yes you could, however;
1) You might want to connect your iPhone to an external power source,
2) You will need to do some testing in how accessible your iPhone will be from (for example) home.
3) 3G is not the fastest, so you’d have to test if speed is acceptable.
Usually, a smartphone in a 3G or 4G network gets an IP address, which should be accessible from your computer at home. I have not yet used this, so some experimentation might be needed. Check out my article on how to repurpose an old iPhone as a security camera.
hans
Hi,
First of all i would like to say a big thank you. The articale was written very well for a person like myself who has little knowledge of computers to understand . I finally get it know. Thank you.
Sam
Hi Sam,
thank you very much – it’s great to hear that!
Thank you for taking the time to post a thank you note – it’s very much appreciated.
hans